
Servers belonging to an accountancy software firm in Ukraine have been seized by the nation’s police following suspicions that the company, Intellect Service, had helped spread the NotPetya cyber attack.
Intellect Service has denied that its software MeDoc had helped spread the cyber attack, which first appeared to be ransomware, around Ukraine and then on a worldwide scale.
However, security experts have uncovered signs that some of the initial infections of NotPetya were spread through a malicious update to Intellect Service’s MeDoc systems.
It is likely that the MeDoc servers were hacked through the exploitation software vulnerability that had not been patched, and then used as an attack vector for NotPetya, rather than Intellect Service intentionally spreading the malware.
However, according to the Associate Press agency, under the MeDoc brand Intellect Services had released a statement acknowledging it had been hacked then deleted the statement, and branded allegations that it had been the propagator of NotPeya as “clearly erroneous” though ot noted it was working with authorities to tackle the outbreak.
Colonel Serhiy Demydiuk, hed of Ukraine’s cyber crime unit noted that Intellect Service had known about the infection.
“They knew about it,” he told Associated Press. “They were told many times by various anti-virus firms. … For this neglect, the people in this case will face criminal responsibility.”
The nation, gropu or peole behind NotPetya have yet to be idintified, though Ukranine has accused Russia od sponsering the attacks, something the nation has denied.
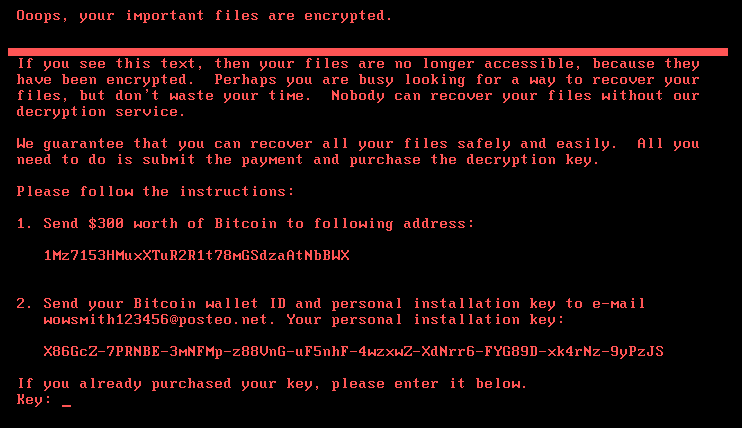
The only activity on the hackers side of things has been the extraction of the Bitcoins in a the wallet they had used to accept ransom payments, though it is unlikely that the people who made the payments will see their data released from the ransomware, as NotPetya contains code that pretty much wiped compromised data rather than locks it.
As such, NotPeya appears to have the potential to cause even more chaos than the WannaCry ransomware if it continues to spread.
OpenAI chief operating officer Brad Lightcap to oversee international expansion as company consolidates lead in…
Chinese researchers publish details on device that could wreak havoc on undersea communications cables in…
Former Intel chief Gelsinger expands role at Gloo, becoming executive chairman and head of technology…
MEPs add to Commission pressure for second EU Chips Act amidst industry calls for renewed…
Smartphone maker Xiaomi reportedly raises about $5.5bn in Hong Kong share sale as it invests…
BYD's Qin L EV sedan starts at about half the price of Tesla's Model 3,…