
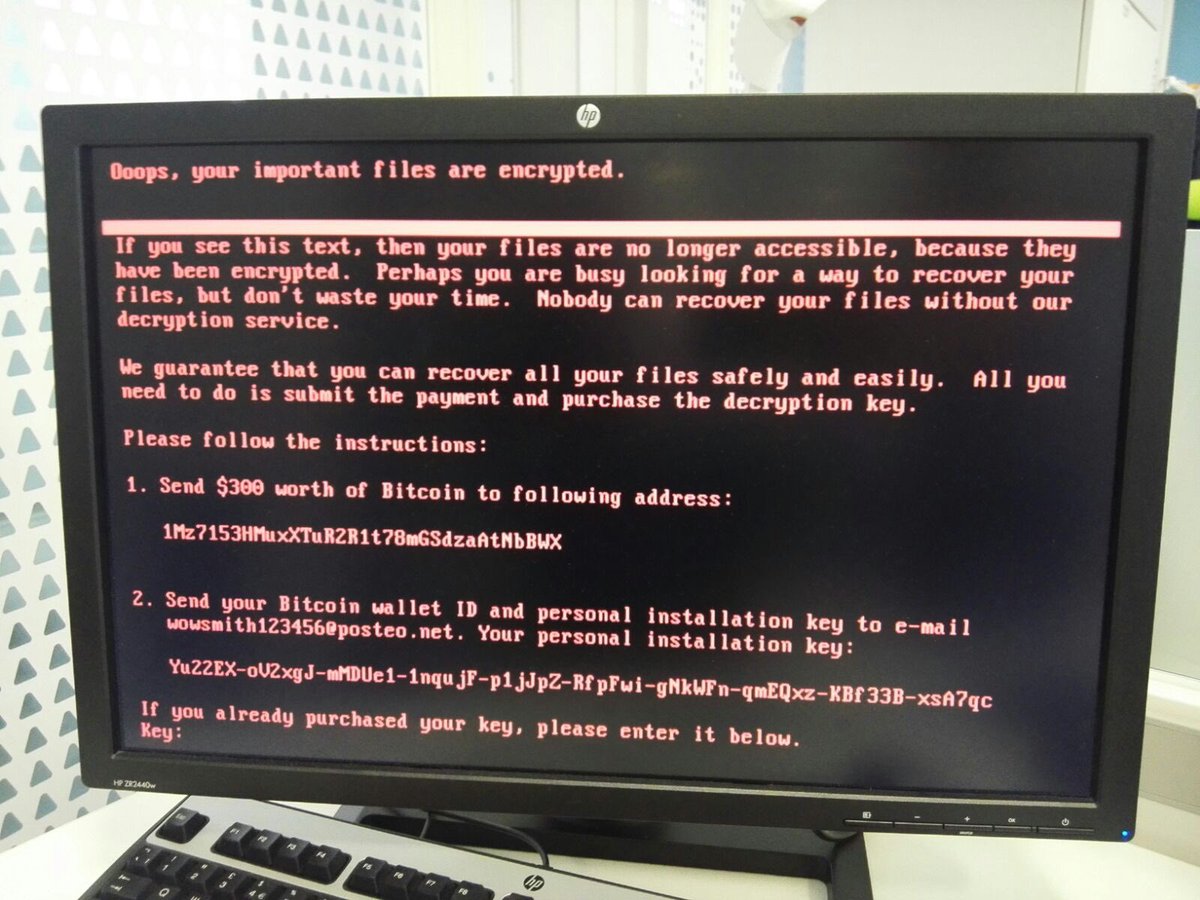
The Petya ransomware.
A ransomware attack is currently spreading like wildfire across the globe, infecting airlines, banks and energy suppliers amongst other organisations.
The attack which originated in the Ukraine has been dubbed by some a ‘NotPetya’ due to its similarities to the previously detected Petya ransomware, thought the current strain has never been seen before according to Kaspersky Labs.
From there the ransomware steals passwords, encrypts files and attempts to gain administrative access to the network the machine is connected to.
ESET researcher Robert Lipovsky likened the spread of NotPetya to that of the WannaCry ransomware.
“For spreading, it appears to be using a combination of the SMB exploit (EternalBlue) used by WannaCry for getting inside the network and then spreading through PsExec for spreading within the network,” he said.
“This dangerous combination may be the reason why this outbreak has spread globally and rapidly, even after the previous outbreaks have generated media headlines and hopefully most vulnerabilities have been patched. It only takes one unpatched computer to get inside the network, and the malware can get administrator rights and spread to other computers.”
Victims of the attack are prompted to part with $300 worth of Bitcoins if they want to be released from the clutches of NotPeyta. Given the ransomware is new, there is a risk that anti-virus programmes may not be able to recognise it in order to stop it.
Numerous major companies have been hit including British advertising and marketing firm WPP, Russian oil giant Rosneft, and Kiiev’s Boryspil Airoprt. Attacks have spread as far as the US, hitting pharmaceutical company Merck and law firm DLA Piper.
Attack telemetry from Kaspersky indicated that more than 2,000 people have been hit by NotPetya so far.
Every cyber security company is advising users of Windows machines to ensure they have their operating system up-to-date, although for organisations with embedded systems this may not be such an easy task.
The Beeping Computer published a way to vaccinate a machine from NotPetya, discovered by Cybereason security researcher Amit Serper, by creating a read-only file names ‘perfc’ in the C:\Windows folder, which prevents a computer from being infected by the ransomware.
Unfortunately, a ransomware kill switch for infected machines has not yet been discovered, and Serper’s solution can only protect individual machines not entire notworks.
“Although the worm is camouflaged to look like the infamous Petya ransomware, it has an extremely poor payment pipeline. There is a single hardcoded BTC wallet and the instructions require sending an email with a large amount of complex strings (something that a novice computer victim is unlikely to get right.),” said pseudo-anonymous information security researcher the grugq.
“If this well engineered and highly crafted worm was meant to generate revenue, this payment pipeline was possibly the worst of all options (short of “send a personal cheque to: Petya Payments, PO Box …”)
“The superficial resemblance to Petya is only skin deep. Although there is significant code sharing, the real Petya was a criminal enterprise for making money. This is definitely not designed to make money. This is designed to spread fast and cause damage, with a plausibly deniable cover of ‘ransomware’.”
As such, it would appear that NotPetya is more an exercise in chaos generation by an organisation or nation looking to test their malware making capabilities.
The Ukraine, which has been hit the heaviest by NotPetya, has pointed blame at Russia. Relations between the two nations are tense following the annexation of Crimea.
However, Russian companies also got caught up in the NotPeyta attack, which would indicate the attack was not one made by a Russian state-sponsored group, unless of course it spiralled out of control as such attacks can do.
There is still a lot of on going research into NotPeyta as the cyber attack unfolds, suffice to say more answers are likely to surface once its spread has abated, though there is a change that it could become a larger and more damaging attack than WannaCry, meaning it could be some time before NotPetya is properly dissected.
Threats like NotPetya serve to show the cyber security world is getting ever more complex, as Silicon found out during interviews on our stand at Infosecurity 2017.
There we spoke with Lastline on machine learning in cyber security, and gained insight from ESET on tackling ransomware and botnets.
American space agency prepares for testing of Boeing's Starliner, to ensure it has two space…
As UK and Europe develop closer military ties, European Commission says it will invest €1.3…
Zuckerberg seeks to revive Facebook's original spirit, as Meta launches Facebook Friends tab, so users…
Notable development for Meta, after appeal against 2021 WhatsApp privacy fine is backed by advisor…
First sign of shake-up under new CEO Lip-Bu Tan? Three Intel board members confirm they…
Trump's nominee for SEC Chairman, Paul Atkins, has pledged a “rational, coherent, and principled approach”…