The National Cyber Security Centre (NCSC) has warned of a scam campaign affecting Android smartphones that can steal banking details another sensitive data.
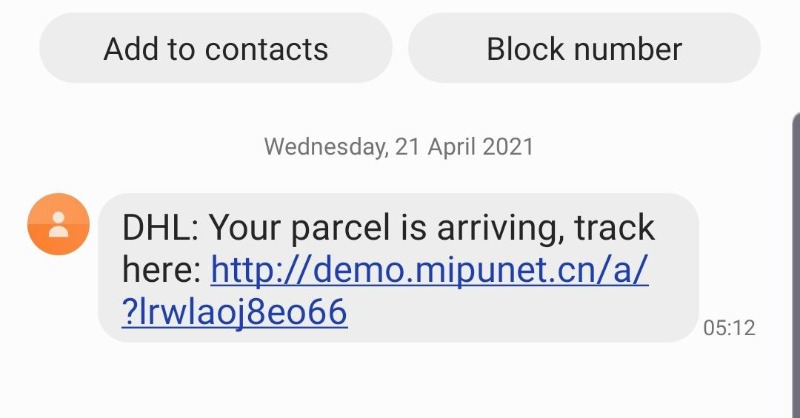
The scam is carried out via text messages that appear to be from a delivery firm, and ask the user to install software to track a parcel.
Instead, the package installs the Flubot malware, which tries to steal banking and other information.
Flubot can also intercept text messages in order to receive one-time passwords from banks and forward them to the attackers.
Phone number theft
The malware furthermore forwards user’s list of contacts to the scammers’ control centre so that it can be targeted by further messages.
Security researchers and mobile phone network operators said the Flubot scam messages began targeting UK users on a massive scale late last week.
“We believe this current wave of Flubot malware SMS attacks will gain serious traction very quickly, and it’s something that needs awareness to stop the spread,” Vodafone said in a statement.
The operator warned that users should be “especially vigilant” with the malware and should be wary of clicking on any links in a text message.
The messages have been sent to millions of users on all networks, Vodafone said.
In an alert on Twitter, Vodafone posted an image of the suspect text message and advised users to forward suspicious messages to 7726 to report them, then to delete them.
EE, Three and other UK networks issued similar warnings.

Scam URLs
The NCSC said there are steps users can take even if they have already fallen for the scam.
“If users have clicked a malicious link it’s important not to panic – there are actionable steps they can take to protect their devices and their accounts,” the agency stated.
Security researcher Paul Morrison said in an advisory the malware uses a wide range of scam URLs that are embedded in the text message.
When visited by an Android device, they display a page appearing to be that of a delivery courier, such as DHL or FedEx, with instructions on how to download and install a parcel-tracking app.
Installing apps outside the official Google Play Store is disabled by default, but users can enable the process in their settings.
Morrison said the complex process is likely to lead to a low success rate, but that with the number of SMS messages being sent out “just a 0.1 percent success rate could be very profitable”.
In a study of Flubot published in early March, Swiss computer security firm Prodaft found that Flubot had already infected more than 60,000 devices and stolen more than 11 million phone numbers.
Phone number theft
Prodaft noted that 11 million is 25 percent of the entire population of Spain, the country that Flubot was targeting at the time.
“We estimate that the malware is capable to collect almost all phone numbers in Spain within six months’ time if no action is taken,” the company’s researchers wrote.
Prodaft noted that the use of stolen contact lists to send the malware via SMS messages was a novelty distinguishing it from other banking malware.
It said the malware’s spreading techniques and its algorithm for generating malicious domains make Flubot “almost impossible” to block using existing techniques.
Flubot has since spread to countries including Germany, Poland and Hungary before arriving in the UK.
Morrison said that while tools exist for removing the malware, he recommends backing up important data and resetting the affected device to factory settings.




