The Cerber ransomware is being delivered to specific countries in Asia, most notably South Korea, according to recent telemetry of the Magnitude exploit kit.
That is the warning from security specialists Malwarebytes, which said that South Korea is the most impacted country amid a slew of ongoing malvertising campaigns.
It should be remembered that the Magnitude exploit kit has been around for a number of years now. In 2014 it was found to be popular among cyber criminals, thanks to its high success probability and an innovative distribution model that didn’t require ‘customers’ to make a downpayment.
Evolving Gate
‘Malvertising’ threats have proven to be a growing area in the cybersecurity field over the past few years as more and more sites depend on adverts for revenue.
Essentially, malverts are when a visitor goes to a website and they are may be exposed to malicious advertising. This happens when criminals have won the trust of an ad agency before packaging the exploit in the advert itself.
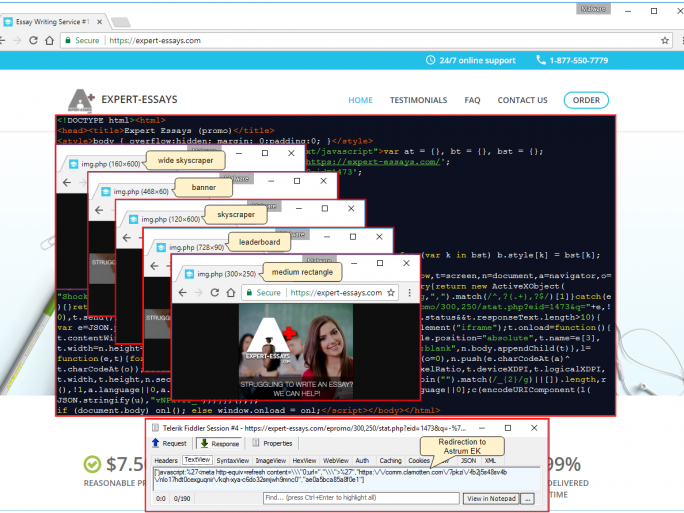
Malwarebytes points out that in addition to traffic filtering performed by various ad networks, users are inspected at a ‘gate’ that decides whether or not they should be allowed to proceed to Magnitude EK.
This gate has already been nicknamed ‘Magnigate’ by Proofpoint, performs additional checks on the visitor’s IP address and user-agent to determine their geolocation, ISP, operating system and browser information.
According to Malwarebytes, in the Autumn of 2016, an important change happened with Magnitude EK as it was no longer rented as a toolkit, but instead became the sole use of one actor who decided to focus on targeting Asia, and in particular, South Korea, delivering the Cerber ransomware.
And since that time, this sole actor has been modifying and obfuscating the code of Magnigate to make it harder to detect and capture the Magnitude EK in the wild.
“A gate is not required in order to perform a successful drive-by infection so long as there is an existing redirection mechanism in place (via compromised sites or malvertising),” said Malwarebytes.
“However, gates provide an efficient way to do final traffic filtering before wasting resources on non-intended targets,” the researchers said. “It’s also a very effective means of preventing honeypots and security researchers from poking their nose into your business or perhaps tracking and logging their activity.”
“It’s quite likely that Magnigate will continue to evolve but the question is whether these will be slight cosmetic changes (different obfuscation techniques) or more substantial (new detection or evasion techniques),” it concluded.
Malvertising Campaigns
Last month Malwarebytes also discovered a large malvertising campaign using the Astrum exploit kit to spread malware to unsuspecting users as they browse the web.
Malwarebytes says the attackers had been “going to great lengths to be as stealthy as possible” and has successfully fooled advertising networks into displaying malicious ads.
It said at the time that while not as sensational as the latest ransomware attacks, malvertising continues to affect users on a large scale and be a relied upon infection vector for threat actors.
Quiz: The world of cyber security in 2017