The NHS Could Have Avoided WannaCry Attack, Says NAO Report

WannaCry ransomware attack made worse as NHS did not follow basic security recommendations
The NHS and the Department for Health have been criticised after Britain’s National Audit Office (NAO) said that it could have avoided the devastating effects of the “relatively unsophisticated” WannaCry ransomware outbreak in May, if they had followed “basic IT security” protocols.
This was the conclusion of the NAO in its report on the matter, which found the cyberattack resulted in a staggering 19,500 medical appointments being cancelled across the NHS.
Additionally, the attack resulted in PCs at 600 GP surgeries being locked, and five hospitals were forced to divert ambulances elsewhere.
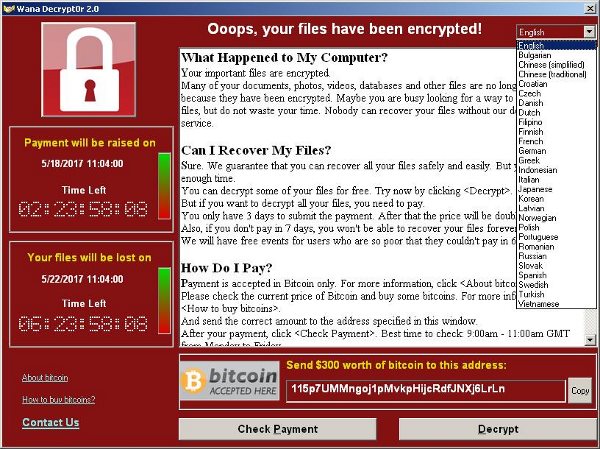
Basic IT Security
The report found that the NHS had been warned about the risks of cyber attacks on the NHS a year before the WannaCry attack in May 2017, but it only responded with a written report in July this year.
The attack led to disruption in at least 34 percent of trusts in England, as at least 81 out of 236 trusts across England were affected in total.
A further 603 primary care and other NHS organisations were infected by WannaCry, including 595 GP practices.
No patient data is believed to have been compromised or stolen, and there is no evidence that any NHS organisation paid the ransom, but the actual cost of the attack remains unknown.
“The WannaCry cyber attack had potentially serious implications for the NHS and its ability to provide care to patients,” said Amyas Morse, head of the National Audit Office. “It was a relatively unsophisticated attack and could have been prevented by the NHS following basic IT security best practice. There are more sophisticated cyber threats out there than WannaCry so the Department and the NHS need to get their act together to ensure the NHS is better protected against future attacks.”
The damage from the WannaCry attack would have been much worse but for the actions of young security researcher, Marcus Hutchins. He found and activated a “kill switch” that prevented future infections from locking devices.
Hutchins was subsequently arrested in the United States and has pleaded not guilty to charges of developing and distributing the ‘Kronos’ banking malware.
Earlier this week NHS Lanarkshire, one worst-hit health authorities in Scotland, admitted that it had failed to ensure its IT systems were fully patched with a vital security update, which left it vulnerable to the attack.
Matters were not helped by the fact that this Scottish health board was still using 395 PCs that ran Windows XP – support for which had ended back in 2014.
North Korea
Meanwhile British officials continue to point the finger of blame towards North Korea for the WannCry cyber-attack.
The UK government has previously said that North Korea was using the ransomware to make money for its totalitarian regime. The nation has refuted such accusations
But the UK remains convinced that the piranha nation was behind the attack.
Speaking on the BBC’s Today programme on Friday, the security minister Ben Wallace said the government believes a North Korean hacking group was responsible.
“This attack, we believe quite strongly that this came from a foreign state,” Wallace reportedly said. Adding that the state involved was North Korea.
“We can be as sure as possible,” he said. “I obviously can’t go into the detail of intelligence, but it is widely believed in the community and across a number of countries that North Korea had taken this role.”
Wallace did not confirm whether the UK would carry out retaliatory attacks, saying it would be “challenging” to arrest anyone when a “hostile state” was involved.
Do you know all about security in 2017? Try our quiz!